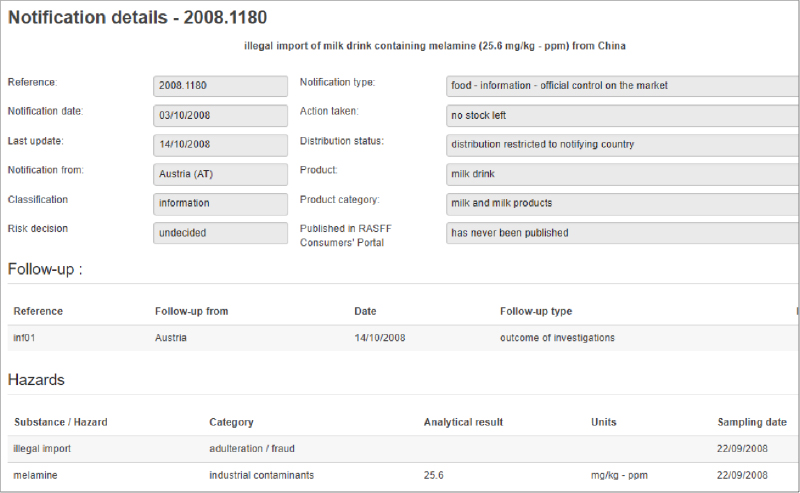
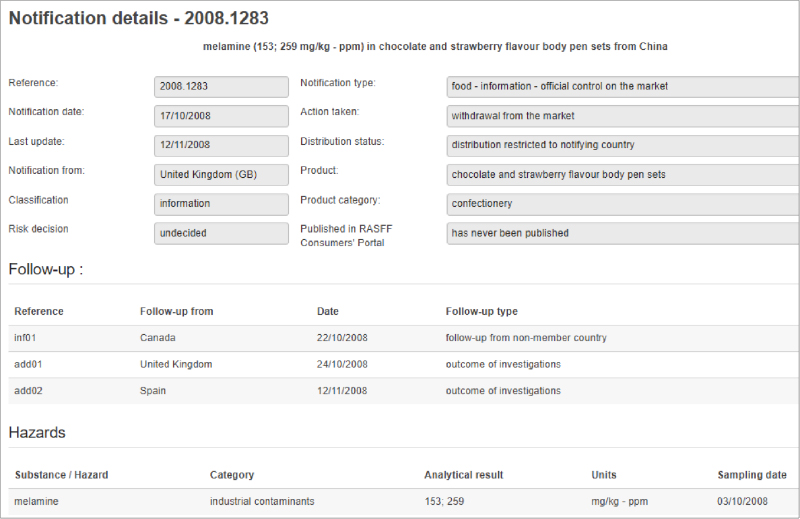
Issues with the health of frontline workers, supply chain disruptions, and changes in consumer behavior are just a few vulnerabilities that the food industry is experiencing as a result of COVID-19. Food Safety Tech recently had a conversation with Jennifer van de Ligt, Ph.D., director of the University of Minnesota Integrated Food Systems Leadership Program and Food Protection and Defense Institute about the hurdles that the industry is experiencing and where we go from here.
Food Safety Tech: What challenges is the food system facing in light of the COVID-19 pandemic? Where are the vulnerabilities?
Jennifer van de Ligt, Ph.D.: The food system is facing primary, secondary and tertiary challenges right now. I see two main drivers as disruptors as a result of COVID-19. The health and safety of employees is the first primary driver. As COVID-19 has more broadly spread through the U.S., ensuring the health and safety of employees in the food system has become essential; however, the pandemic has shown us the food system has struggled with that.
The other big primary challenge facing the food system has been the swift change in consumer behavior. Pre-COVID-19, nearly half of food was consumed away from home. When restaurants closed, and stay-at-home orders were in place, it put extreme amounts of pressure on our food retail segment, causing supply and demand issues.
Regarding the health and safety of employees: We’ve seen meat processing struggle with production demands because the health of their employees has been impacted by the virus. In mid-April, the beef and pork capacity in this country went down by over 40%. They are making great improvements and are approaching normal harvest capacity range for both [beef and pork production]. Meat cuts being produced are slightly different than normal, as this part of the meat plants are very labor intensive. This has really highlighted the need to make sure that we keep the health and safety of our food system employees front and center.
During the 2020 Food Safety Consortium Virtual Conference Series, Jennifer Van de Ligt will participate in a panel discussion on November 5 about Professional Development and Women in Food Safety | Register Now Now that the meat supply chain is beginning to recover, we’re also beginning to see increasing effects on non-meat supply manufacturing. This isn’t isolated to food manufacturing; as we experience broader community spread, COVID-19 will impact all aspects of our food system.
On consumer behavior: As consumers shifted to food retail, immense pressure was quickly put on our food supply chain logistics, manufacturing timing and processes, the speed to warehouses and delivery, etc.
One example that demonstrates a challenge in manufacturing and consumer demand is the difference in volumes for food services versus retail. I like to use the example of shredded cheese. At a grocery store, you’ll find a one-pound pack, but shredded cheese in food service might be in a 10-pound bag. There are not a lot of consumers who want to buy a 10-pound bag of shredded cheese. Well, why can’t cheese manufacturers just package bulk product into one-pound packs? There are several reasons that don’t allow producers to pivot quickly: They may not have the machinery or packaging to do that. Also, changing packaging from food service to retail requires different labels and regulatory approvals. Examples like this led to many of the spot outages consumers found in grocery stores. In the produce sector, it led to produce being plowed under in fields because they didn’t have the distribution channels to go into retail instead of into food service.
In the Integrated Food System Leadership (IFSL) program, we’ve recently discussed food equity and food injustice as a result of COVID-19. As food retail became stressed and unemployment increased, we saw a huge demand for our food assistance networks. Because food retail is one of the primary contributors to the food assistance networks, there wasn’t enough volume being donated. In addition, food service foods are not appropriately packaged to go into the food assistance networks and food banks, similar to the issue in moving to food retail. This led to tremendous pressure and innovative solutions to source and distribute food to a newly vulnerable population.
As we look ahead into the coming months, many of the vulnerabilities in the food system will be the same. We have to continuously monitor the health and safety of our employees to keep our food system as a whole functional. There’s a growing recognition that our primary agriculture workers are also at risk—the people in fields harvesting and planting. There are many groups providing recommendations on how to protect agriculture employees and communities where they work and reside.
We’ll see continued adaptation in the food system to the new reality of how restaurants and food service engage with their consumers with the shift in behavior to limited restaurant dining and increases in online ordering.
FST: In what areas do food manufacturers, processors or growers need to adapt moving forward in order to thrive?
Van de Ligt: There are several. First, I think this crisis has really brought worker health and welfare to the forefront, and there will be more emphasis on the essentiality of food system workers. They were previously a behind-the-scenes workforce. The issue of worker health and welfare is going to accelerate in many industries, but I also see a push to more automation. The human workforce is necessary, and people do a really wonderful job, but are there areas that might benefit from automation? I think those go hand in hand.
I also think the global food system needs to rethink how it remains resilient. In the past, there’s been a focus on resilience and efficiency through economy of scale. That still exists and may look different moving forward. Using the meat industry as an example, that economy of scale was also its biggest weakness that had gone unrecognized. Going forward, I think there are many companies that are going to consider alternative supply chains. Should multiple, smaller plants be utilized instead of one large plant to provide a more resilient framework for production? Other companies are going to think about installing equipment or processing lines that could more quickly pivot between food service and food retail. There’s also a huge opportunity now for local and smaller markets to really make an impact as people look for alternative supply chains and sources. We found that many of the local food markets and co-ops, especially those that provided into food service, pivoted pretty quickly to pop-up online marketplaces to provide food direct to consumer. I think we’ll see that trend increase as well.
In order to feed billions of people worldwide, it’s essential that the food industry take a broader systems approach versus the siloed approach path we’ve been using. The pandemic has highlighted how the food system is an intricately functioning balance and requires collaboration. Our food system will only be able to move forward faster with less disruption when we have food system leaders who understand the intricacies and the ripple effects of the challenges we face. Leaders who understand the impacts of decisions outside of their sphere will be essential to plan for impacts from natural disasters, another pandemic, etc.—and to create a more responsive and resilient food system in the future.
FST: Where does this leave folks who are either beginning or rising in their careers in food safety? Do you think the pandemic has changed food safety careers as they’ve historically functioned?
Van de Ligt: I like to say that ‘what got us here is not going to get us there.’ In general, if you think about where food safety careers have been in the past, the roles have been all about consistency, understanding regulations, making sure we do everything precisely right all of the time so we don’t have a food safety outbreak.
The focus on doing things precisely right all of the time will absolutely continue. What I think will shift is the need for food safety professionals to think more broadly than just the regulations that are required for compliance. Food safety professionals need to understand more about the system that is happening outside their facility; the impact of their work going backwards and forwards in the supply chain.
How things have worked historically in a food safety role has been having a consistent supplier network that provides the same type of product every time; you know what to expect, how to produce and distribute safe food for the customers you serve. In a situation like COVID-19, because of the disruptions from farm to fork, the suppliers you need to work with may be different and you need to quickly make decisions spontaneously as supply shifts. Having the knowledge and skills to navigate changes is essential to ensure the quality and safety of your product.
A highly technical focus that many professionals have when they start their career is often too narrow and won’t be enough for emerging food system leaders. Leadership skills are vital as well. In the IFSL program we teach food system professionals how to explore proactive viewpoints, not just managing people or responsibilities. Managers make sure things are done things correctly; leaders make sure we do the right thing. In order to learn how to do the right thing, we teach skills and tools on how to navigate uncertainty; practicing active listening, constructive feedback; and understanding the concerns of a supplier or customer are examples.
We emphasize and teach in the IFSL program that food system professionals and leaders need to be much more proactive. This means equipping them with the food system knowledge and leadership skills so they can predict and prepare for how decisions affect upstream and downstream. Having a broader viewpoint is critical to adaptivity, which will build resilience and help limit disruption.