In 2016, the food authenticity team at Queen’s University Belfast published a study that evaluated adulteration levels in oregano—specifically, 78 samples purchased at retail.1 Almost a quarter of the samples had some adulteration. Some samples actually contained more than 70% other leaf material, primarily olive and myrtle leaves. This study was widely reported and appeared to result in drastic decreases in the levels of adulteration in oregano.
However, just last year, the Joint Research Centre of the European Commission published the results of a coordinated control plan for “fraudulent practices” in spices in which they tested 1,885 samples of 6 herbs and spices submitted from from 23 countries.2 Almost half of the 295 oregano samples were “suspicious of being adulterated.” The results of these studies imply that food fraud—especially fraud involving higher-value and further-processed products with a substance that does not make consumers sick—is a persistent risk and demands a sustained response from industry and regulators.
Evaluating historical data from various sources (the scientific literature, regulatory reports, media reports, etc.) is a critical component of a food fraud prevention program, but it is not enough. A strong program will include an in-depth evaluation of what is known historically about food fraud for relevant raw materials, ongoing monitoring of food safety and fraud notifications, a fraud-focused evaluation of supplier controls, audit and testing programs that include specific anti-fraud measures, and an assessment of situational factors that could increase fraud incentive (geographic, economic, etc.).
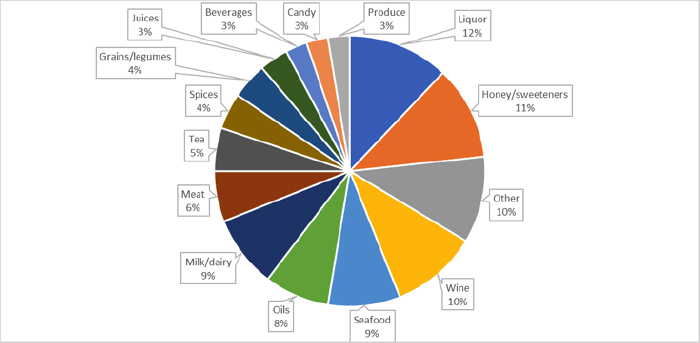
The Food Fraud Database has tracked public reports of food fraud for almost 10 years. Many incidents are types of fraud that have occurred repeatedly, as the incident distribution from last year illustrates (see Figure 1). In addition to herb/spice fraud, frequent types of fraud include replacement of honey with sugar syrups; unregulated and counterfeit liquor; wines labeled as a more expensive varietal or with undeclared additives; milk products with added protein or fats from other sources; and fraud related to organic certification or geographic origin. Although these types of fraud appear to be “reasonably foreseeable,” the challenge is that during a time of supply chain stressors—such as the COVID-19 pandemic—risks may evolve quickly as suppliers and supply chain structures change. Re-evaluating food fraud vulnerability in response to changing conditions can be time-consuming, but is important to stay ahead of potential risks.
We frequently work with food manufacturers to develop their food fraud vulnerability assessments. Our experience is that searching and compiling risk data and mapping a set of raw materials to the appropriate data sources for analysis can be the most time-consuming aspects of the project. Since Google searches or other manual processes are not always reliable and efficient, a helpful first step can be finding a data source that compiles and standardizes food safety and fraud data from a wide range of reliable sources. The mapping process then involves identifying each individual ingredient component of the raw materials sourced by the company and linking it to the relevant ingredient name in the data source. It is important to invest this time up front to identify the most appropriate data sources and conduct a thorough mapping process. This ensures food safety and quality assurance staff will be notified of information relevant to their particular supply chains moving forward.
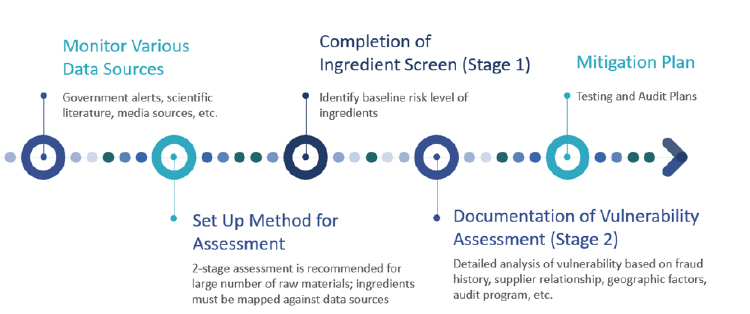
Many quality assurance professionals struggle to fit in food fraud assessments and mitigation plans while managing day-to-day food safety and quality programs. A two-stage process, including an ingredient screen followed by a detailed assessment for potentially high-risk ingredients, can make the process more efficient for companies managing hundreds of raw materials (see Figure 2). Existing food safety testing and auditing programs may also have application to food fraud prevention and should also be documented in a food fraud program. Many food companies find value in outside expert guidance to set up a food fraud program so that food safety and fraud risks aren’t unintentionally missed. The goal of a food fraud program is not to add to the workload of food safety and quality assurance staff, but to enable those staff to identify the most targeted measures that will help ensure food safety, authenticity, and brand protection.
References
- Black, C., et al. (2016). A comprehensive strategy to detect the fraudulent adulteration of herbs: The oregano approach. Food Chemistry, 210, 551–557. https://doi.org/10.1016/j.foodchem.2016.05.004
- Maquet, A., et al. (2021). Results of an EU wide coordinated control plan to establish the prevalence of fraudulent practices in the marketing of herbs and spices. EUR 30877 EN. Publications Office of the European Union, Luxembourg. ISBN 978-92-76-42979-1 (online).









