Birds of different species can become a pest problem depending upon where they are landing, roosting or nesting. In terms of food facilities, birds can cause various concerns: Product safety risks, possible contamination (bird droppings/feathers), poor audit grades, inspection failure, secondary insect pest problems, vectoring of foodborne illness pathogens, plant closures or fines. It is for these reasons that it is essential that food, beverage and product manufacturers (FBP) establish an integrated bird management (IBM) program.
An IBM program will ensure that every essential team member is on the same page in terms of the protocols for managing pest birds within and around the facility. Even if a facility has taken a proactive approach to bird control, the potential exists for birds to enter a facility. Especially considering bird pressures around adjacent properties, buildings, bodies of water and food sources near the facility.
Read Part I of this series: Bird Problems and Control Methods for Food Production FacilitiesIBM for food industry facilities is a systematic approach to preventing birds from gaining access within a facility and reducing the length of time birds remain within a facility. Nuisance birds, depending upon how severe the bird pressure—i.e., how many birds are landing, roosting and/or nesting within a given area—can cause severe damage to equipment, property, food products, displays, vegetation, façade signage, ledges, roofs, HVAC equipment, drains, fire suppression, electrical equipment and more. The longer that birds are permitted to remain within and around a facility, the more damage they can cause, and the harder it is to remedy the problem. Thus, it is critical to remove any birds that have gained entry as soon as possible to prevent possible FBP contamination and the birds getting comfortable within the facility.
There are several components to developing an IBM program. First, you need to conduct a complete inspection of the interior/exterior of the facility, followed by a review of the current data as well as any historical bird data. Now that you have all the raw data, you can begin developing the site-specific IBM plan for the FBP facility. Now that you have the program designed, the program can be implemented. Finally, after a defined timeframe that the IBM program has been active, the program needs to be evaluated to determine if any adjustments need to be made to the program.
Inspection
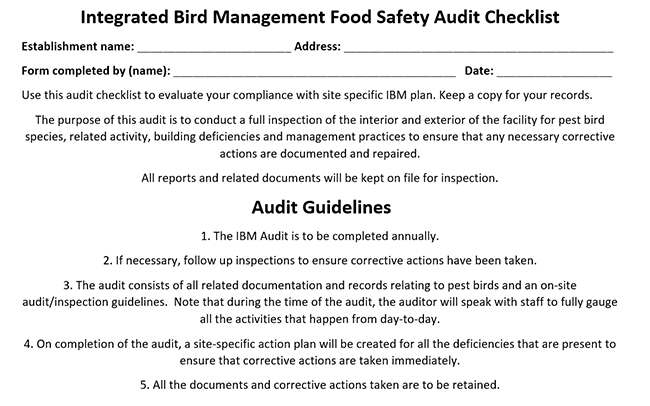
The first step in developing an IBM program is to conduct an initial site inspection audit of the interior and exterior of the facility.
|
|
The following various elements need to be inspected and with said findings documented.

On the interior of the facility, look at the following items:
- Active Birds with the Facility
- List the areas and locations of birds
- Example: Location(s): Food prep area(s), warehouse, etc.
- Any history of birds and related areas
- List the areas and locations of birds
- Interior Landscaping
- Type(s) and necessity
- Food Processing Areas
- Any active control measures in place
- Assess the level of risk
- Bay Doors
- Location(s): Gaps
- Location(s): Bumpers
- General Doors
- Location(s): Gaps
- Location(s): Bumpers
- Location(s): Structural
- Location(s): Doors left open
- Additional Access Point(s)
- Check all equipment areas that enter/exit building
- Pipe-Line Penetrations
- Sanitation
- Conductive Conditions
- Location(s): Standing water
- Location(s): Food Sources
- Debris
- Bird Droppings or Nesting Materials
- Staff feeding birds
- All access to food and water

On the exterior of the facility, look at the following items:
- Active birds with the facility
- List the areas and locations of birds
- Example: Locations(s): Rear loading dock
- Any history of birds around the exterior of the facility
- List the areas and locations of birds
- Adjacent Structures
- Accessory buildings and structures
- Sanitation Practices (Exterior)
- Location(s): Dumpsters
- Exposed food sources and spillage
- Trash Receptacles
- Trash Removal Frequency
- Food Waste on Ground
- Cleaning Practices
- Cleaning Practices Schedule
- Cleaning Food Waste Bins
- Motion Doors
- Bay Doors (Exterior)
- Location(s): Gaps
- Location(s): Bumpers
- Location(s): Structural
- General Doors (Exterior)
- Location(s) Doors Being Left Open
- Additional Access Point(s)
- Bodies of Water
- Conductive Conditions
- Structural (Exterior)
- Location(s): Pipe-Line Penetrations
- Location(s): Flashing
- Location(s): Pipes
- Location(s): Openings
- Location(s): Roof
- Location(s): Roof Hatches
- Location(s): Windows
- Location(s): Canopy (Front/Rear)
- Location(s): Awnings (Front/Rear)
- Location(s): Façade Signage (Front/Rear/Side)
- Drainage
- Standing Water
- Clogged Drains
- Landscaping
- Retention ponds
- Bird Droppings or Nesting Materials
- Exterior Storage
- Merchandise Displays
- Existing Bird Control Devices
Review
Next, after all the above items have been inspected and findings recorded, all the data needs to be reviewed. In addtion, all the current bird management practices within the facility, documentation practices, and current audit/inspection findings should be all evaluated together. All this information is your road map for developing your IBM Program. Make sure that while you are collecting all the said raw data, you also speak with all necessary staff to get the most accurate information possible.
Documentation
Now that you have conducted your inspections and collected all the data, it’s time to create a site-specific IBM Policy & Plan for the facility. The development and implementation of the IBM plan will provide the appropriate procedures that are to be implemented to prevent, control and exclude birds from entering a facility and from keeping birds an acceptable distance away from the facility. With proper training and implementation of IBM procedures, there will be a reduced likelihood that birds will be able to enter the facility, and the length of time birds remain inside the facility will be reduced—thus, reducing the level of pest bird damage caused, reducing hazards to food sources, equipment, the public, and the facility environment.
Each facility is unique in its operation, location and potential for bird activity. The facility’s IBM plan will be designed to factor its control options when remedying and preventing bird pressure.
Implementation
Now that you have an IBM Plan, it’s time to implement the plan. First, make any necessary changes based upon findings of the audit and review of all data. Next, correct any conducive conditions that were discovered during the inspection. All the items that may require adjustment may need to be planned out depending upon budgetary constraints. Define staff roles regarding bird control efforts on a front-line facility level. Each member of the action team must fully understand their role and responsibility about the implementation and day-to-day operation of the plan.
The IBM Plan is the roadmap that should be followed for managing pest birds throughout the interior and exterior of the facility and related structures. It will set forth the facility’s bird threshold levels and site-specific facility needs. Furthermore, the IBM Plan will provide in detail how each phase of the plan will be implemented at each facility. The facility coordinator, in collaboration with the IBM coordinator, shall be responsible for the administration and implementation of the IBM plan. Each of their roles and responsibly should be thoroughly reviewed and understood.
Next, conduct staff training on proper bird control removal methods if handing live removal internally. Otherwise, what are the approved processes for third-party vendors who are providing removal services? Finally, conduct a review of the new documentation process to record all necessary data for the IBM program. Data collection is a critical component in evaluating the success of the plan and determining if any adjustments need to be made.
Evaluation
To ensure goal compliance, the IBM program should be evaluated at each site annually. The review must consist of all records, the number of birds that gained access into the store, corrective actions taken (at the facility level and outside efforts), and any plan adjustments. By reviewing all the data collected, the plan’s effectiveness can be determined, and whether alterations need to be made. Note that the IBM plan is not a static document that sits in a binder. The plan will have to evolve as operations change, or the set goals of the program are not met.
Conclusion
A proactive approach to reducing bird populations is critical for food industry facilities. As such, the IBM program will ensure that your entire staff is adequately trained on all the site-specific bird control methods, reduce the frequency of birds entering the facility and create a documented bird control program that is designed for your specific facility.