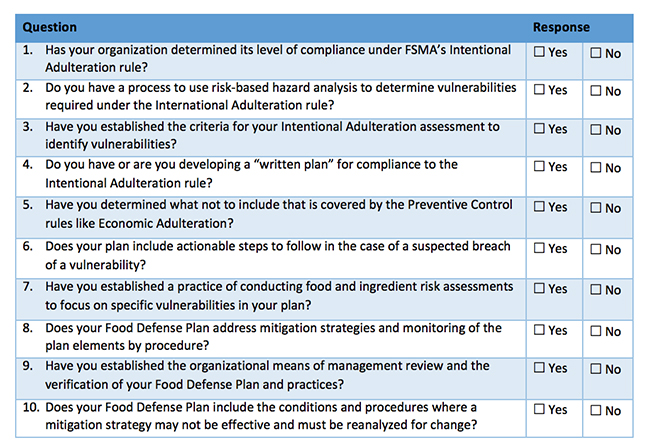
Food defense is the effort to protect food from intentional acts of adulteration where there is an intent to cause harm. Like counterterrorism laws for many industries, the IA rule, which established a compliance framework for regulated facilities, requires that these facilities prepare a security plan—in this case, a food defense plan—and conduct a vulnerability assessment (VA) to identify significant vulnerabilities that, if exploited, might cause widescale harm to public health, as defined by the FDA. Lessons learned during the conduct of food defense vulnerability and risk assessments and the preparation of the required food defense plan are detailed throughout this three-part series of articles. Part I of this series addressed the importance of a physical security expert, insider threat detection programs, actionable process steps (APS) and varying approaches to a VA. Part II reviewed access, subject matter experts, mitigation strategies and community drinking water. This final article reviews broad mitigation strategies, feasibility assessments, food defense plans, partial ingredient security and the “Three Element” approach through more lessons learned from assessments conducted for the largest and most complex global food and beverage facilities, but which can also be applied to the smaller facilities that are currently in the process of readying for the next deadline of July 26.
Lesson 14: When the final rule was released, the concept of using broad mitigation strategies was eliminated. That notwithstanding and realizing that many companies seek to operate at a stricter standard for food defense with a clear focus on brand protection, versus only those process steps that potentially could result in a “wide scale public health impact.” Broad or facility-wide mitigation strategies should not be abandoned, but are less likely to get you a lot of credit for IA compliance. Including existing food safety prerequisite programs (PRP), programs and practices that are put in place to maintain a sanitary environment and minimize the risk of introducing a food safety hazard, can, in some cases, also be included as security mitigation. PRP’s with slight modifications can also contribute to a good “food defense” posture. For example, one PRP addresses hazardous chemicals and toxic substances. In some cases, non-food grade substances that could result in product contamination (not necessarily wide-scale public health impact) might be available to a disgruntled insider. It is obvious companies are concerned about contaminants being brought into the plants, but please do not overlook contaminants that are already there and ensure that they are properly secured when not in use.
Other facility-wide programs (broad mitigation) that contribute to effective food defense might include site perimeter or building security, visitor and contractor management, pre-employment background checks, employee security awareness and food defense training and sanitation chemical management.
Lesson 15: If you are using the three elements approach (Guidance Chapter 2 Section G) or the hybrid approach (Guidance Chapter 2 Section H), you will be required to make an assessment on feasibility. In the early VA’s conducted, prior to the second installment of the guidance in March of 2019, feasibility was essentially an all or nothing proposition. One could argue that a judgment call was required as to whether an intentional adulteration incident could be accomplished given the inherent conditions. Those conditions might include a lot of coworkers who might be able to observe and serve as witnesses to deter the act. With the release of the second installment of the guidance from the FDA, a new tool was made available which would allow food and beverage companies to run a calculation and make a more accurate prediction of how much of an unnamed “representative contaminant” which is assumed to be highly lethal and heat stable it might take to contaminate a product batch. Typically, the larger the batch size, the higher the quantity of the “representative contaminant” would be required to achieve a lethal dose (LD) in a serving size. So, to provide an additional level of validation with identified actionable process steps, the use of the LD calculation might be considered to provide more realistic insight into the feasibility element. For instance, if it would require one hundred pounds of the “representative contaminant,” you might feel justified in concluding that it is not realistic to get that amount of contaminant into the batch at the process step and rule out the point, step or procedure as an APS. This can save money and ensure limited food defense resources can be channeled to the areas where legitimate risk can be reduced.
Lesson 16: After an APS is identified, sites will need to determine, as the rule states, whether the existing “mitigation strategies can be applied…to significantly minimize or prevent the significant vulnerability.” Simply stated, what is in place today for food safety, and the broad-based security measures in use, may or may not be enough when you consider an insider motivated to contaminate the product. The FDA’s mitigation strategies database may offer some insights into additional food defense measures to consider. Where additional mitigation strategies are identified, from the time of completion of the VA until a site’s regulatory compliance deadline arrives (next one is July 26, 2020), that change must be incorporated into the food defense plan and fully implemented. We recommend that a site make a list of new mitigation strategies after the VA is complete for tracking purposes during the implementation phase. No mitigation strategies should be included in the food defense plan that are not fully implemented and where records cannot be adequately produced.
Lesson 17: In the second installment of the guidance, the concept of partial ingredients was introduced. The key activity types (KAT) of secondary ingredients is now considered to include the storage of partially used, open containers of secondary ingredients where the tamper-evident packaging has been breached. Tamper evident tape looked to have promising benefits, but several of our clients have abandoned the use of this mitigation strategy, which has been proven repeatedly to be defeated without detection. It appears that using containers that can be secured with numbered seals might be a better option and even better if the seals would be metal detectable in the event one went astray in a product stream.
Lesson 18: Food defense plan unification. Facilities regulated under the IA rule are likely to already have a food defense plan for other initiates such as SQF or BRC. The IA Rule is not unlike other counter-terrorism regulations in potential to create challenges to meet voluntary and regulatory requirements without having multiple food defense plans. The IA Rule based on its modeling after HACCP creates some very specific requirements in terms of how data needs to be presented and records maintained. Sites may be doing other things to support food defense, and one strategy that might keep auditors in their lane would be to include any non-IA Rule food defense content (e.g., for SQF or BRC) in an appendix to the IA Rule Food Defense Plan.
Lesson 19: Under the VA method the FDA refers to as “the “Three Element” approach, suggestion is made in the guidance released in March 2019 that regulated facilities might consider creating stratified categories for each element of public health impact, degree of physical access and ability of the attacker to successfully contaminate product. This is asking regulated facilities to engineer their own vulnerability assessment methodology. It is our opinion that this is asking a lot from a food and beverage facility and that creating categories for each element (e.g., refer to Table 3 on page 54) will extend the time it takes to complete a vulnerability assessment, create a lot more uncertainty in the process and does not necessarily help companies to identify the areas where intentional adulteration risk is highest.
Conclusion
Organizations who have yet to execute vulnerability assessments (due July 26) or those who have already completed vulnerability assessments who may wish to reflect back on their existing VAs in an effort to eliminate unnecessary APS’s should find these strategies helpful in focusing limited resources to the areas where they can have the greatest effect. Since the initiation of this article series, the FDA has released its third installment of the guidance. Once we reflect on this new installment, we will address our thoughts in a future article.